So I was having an issue with my 400 Citrix users printing from Internet Explorer 11. The issue began after upgrading from IE9 to IE11. It was reported that when users attempted to print they would receive only blank pages with page numbers. Receiver for Windows 4.11 for Windows product software. High performance access to Windows virtual apps and desktops, anywhere access from your desktop, start menu, Receiver UI or web access with Chrome, Internet Explorer or Firefox. Hi was hoping someone has some insight on an issue we are having. We have a silverlight out of browser application we are hosting. Inside the application (medical related application) When you select a patient it opens a popup I.E. 11 window from a second application.
This article explains browser content redirection feature in citrix.
Feature Requirements
- Windows 7, 8.x,or 10, and Internet Explorer 11
- Citrix Receiver for Windows 4.10 or higher
- Citrix Receiver for Linux 13.9 or higher

XenApp / XenDesktop 7.16 or higher
- VDA operating system: Windows 10, Windows Server 2012 R2, Windows Server 2016
- Browser on the VDA: Internet Explorer 11 (this is the only supported browser and version)
What is Browser Content Redirection?

Browser Content Redirection prevents the execution/rendering of web pages on the VDA side by creating a corresponding browser instantiated by Receiver that will be responsible for rendering the URL. The browser runs on the endpoint device instead of on the VDA. It will utilize endpoint CPU, GPU and RAM resources and will not require any graphics, video, or animation to be rendered over Thinwire.
Why is Browser Content Redirection Required?
We see very high CPU utilization caused by web browsing on the VDA side. Most problematic are sites incorporating HTML5 video elements. These can be handled by the HTML5 Video Redirection feature, except that it does not yet handle videos streamed using Media Source Extensions (MSE). Sites may eventually incorporate Encrypted Media Extensions (EME), also, which could further complicate video redirection efforts. The most-noticed and complained-about site is YouTube, which is particularly hostile to our HTML5 Video Redirection feature, as it does complicated JavaScript processing and uses MSE extensively.
How Browser Content Redirection Works
This feature is an extension of existing HTML5 Video Redirection components to add support for entire-browser-content redirection, instead of replacing a single video. It is able to manipulate the browser in a way that can intercept page loads, inject our script, monitor for changes to browsing history, and amend it to match the client side.
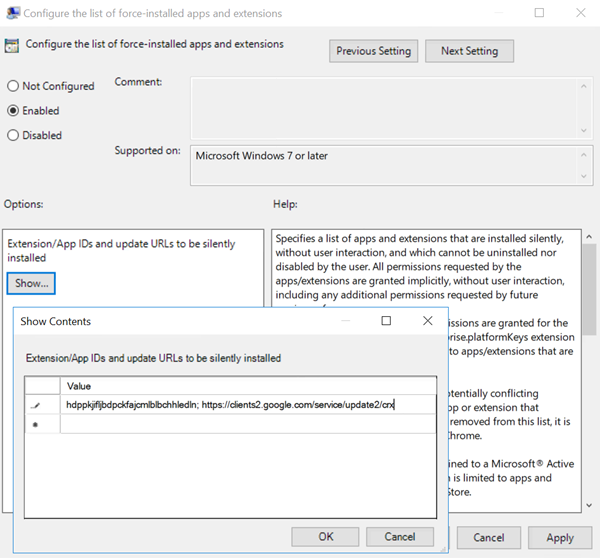
Interaction between VDA and Receiver
- VDA remotes IE 11 Web Browser instance to Receiver via Thinwire. User navigates to a webpage whitelisted in the Studio Policy Browser Content Redirection ACL Configuration. If the webpage has a matching entry in the Browser Content Redirection Blacklist Configuration Studio policy, the viewport will not be redirected to the client.
- The procedure for redirecting webpages is initiated by JavaScript, communicating with an agent in the user’s VDA session over Secure WebSockets. HdxVideo.js is the javascript injected on the whitelisted webpage with the help of Internet Explorer Browser Helper Object (BHO) as the user browses the web on IE11 in the VDA. BHOs are a plugin model for Internet Explorer that provides hooks for browser APIs and allow the plugin to access the Document Object Model (DOM) of the page to control navigation.
- VDA sends instructions to Receiver over a Virtual Channel to instantiate the local overlay browser (HdxBrowser.exe) present on the client.
- Client-Side HdxBrowser.exe retrieves and renders content locally, using client resources instead of those of the VDA.
HTTP/S content can be retrieved directly by Receiver, or through the VDA (see scenarios 2 and 3 below).
There are three scenarios of how Citrix Receiver fetches content:
- Server fetch and server render: There is no redirection because you didn’t whitelist the site through Citrix Studio policies or the redirection failed. We fall back to rendering the webpage on the VDA .High CPU, GPU, RAM, and bandwidth consumption on the VDA.
- Server fetch and client render: Citrix Receiver contacts and fetches content from the web server through the VDA using a virtual channel. This option is useful when the client doesn’t have internet access. Low CPU, GPU and RAM consumption on the VDA, but bandwidth is consumed on the ICA virtual channel. A Proxy Server is required for this scenario (see Policy ‘Browser Content Redirection Proxy Configuration’).
- Client fetch and client render: Because Citrix Receiver contacts the web server directly, it requires internet access. This scenario offloads all the network, CPU,GPU and RAM usage from your XenApp and XenDesktop Site.
Controlling Browser Content Redirection Fallback to the VDA
The existing Windows Media fallback prevention Studio policy supports BCR fallback behavior (as of XenApp And XenDesktop 7.17).
There might be times when client redirection fails. For example, if the client machine does not have direct internet access, an error response might go back to the VDA. In such cases, the Internet Explorer browser on the VDA can then reload and render the page on the server.
Citrix Internet Explorer Plugin
You can suppress server rendering of video elements by using the existing Windows media fallback prevention policy:
Set the Windows Media fallback prevention Studio policy to Play all content only on client or Play only client-accessible content on client:
- These settings block video elements from playing on the server if there are failures in client redirection.
- Setting this policy suppresses only the video elements and not the HTML content of the page. The HTML content is still rendered on the server.
- This policy takes effect only when browser content redirection is enabled and the URL that falls back is in the Access Control List policy.
- The URL can’t be in the blacklist policy
Posted in https://support.citrix.com/article/CTX230051
Fetching takes lot of network resources as it need to pull data(video or any content) from internet and render takes lot of cpu resource as it need to present it over browser. Ex, playing a youtube video. It need to pull video from internet and present it on browser.
More info here: https://docs.citrix.com/en-us/xenapp-and-xendesktop/current-release/multimedia/browser-content-redirection.html
Single Sign-on authentication can be configured on both new and upgraded setup.
| Configuring Single Sign-on on a new Citrix Receiver for Windows setup |
| Configuring Single Sign-on on an upgraded Citrix Receiver for Windows setup |
| Single Sign-on Troubleshooting and Diagnostics |
To configure Single Sign-on on a new setup:
1. Enable User name and password and Domain pass-through on StoreFront or the Web Interface
Depending on the XenApp/XenDesktop deployment, Single Sign-on authentication can be configured on StoreFront or the Web Interface using the Management Console.
StoreFront server: Launch StoreFront Studio, go to Store > Manage Authentication methods > enable Domain pass-through.
Internet Explorer Citrix

Note: Single Sign-on is not supported if Citrix Receiver for Windows is connected to XenApp/XenDesktop using NetScaler Gateway.
| Scenario | Steps | Description |
|---|---|---|
| Configured on StoreFront or the Web Interface with Management Console | StoreFront server: Launch StoreFront Studio, go to Store > Manage Authentication methods > enable Domain pass-through. | When Citrix Receiver for Windows is not configured with Single Sign-on, it automatically switches the authentication method from Domain pass-through to Username and Password, if available. |
| Receiver for Web IS Required | Launch Stores > Receiver for Websites > Manage Authentication methods > enable Domain pass-through. | When Citrix Receiver for Web is not configured to allow Domain pass-through, it automatically switches the authentication method to Username and Password, if available. If you are launching published applications using Internet Explorer for Storeweb, enable the Single Sign-on feature as described in the section Group Policy Settings. |
| StoreFront IS NOT configured | If Web Interface is configured on a XenApp server, open XenApp Services Sites > Authentication Methods > enable Pass-through. | When Citrix Receiver for Windows is not configured with Single Sign-on, it automatically switches the authentication method from Pass-through to Explicit, if available. |
2. Configure XML trust services on the Delivery Controller
On XenDesktop 7 or later or XenApp 7.5 or later, run the following PowerShell command as an administrator on the Delivery Controller:
asnp Citrix*
Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $True
Refer to the Knowledge Center article: Error: 'An error occurred while making the requested connection'.
Note: On XenApp 6.5, XML Service Port and Trust is enabled using the Graphical User Interface. For more information, see Configuring the Citrix XML Service Port and Trust.
3. Modify Internet Explorer settings and Install Citrix Receiver for Windows with Single Sign-on
3.1 Modify the Internet Explorer settings
Modify the Internet Explorer settings to add StoreFront URL or Web Interface URL to the list of Security Zones in Internet Options. There are two methods to modify Security Zones:
NOTE: At any time, use only one of the following methods.
| Option 1 |
|---|
|
| Option 2 |
|---|
Note: Automatic logon with current user name and password can be configured using Group Policy. For more details, see Managing Browser Settings with Group Policy Tools. |
3.2 Install Citrix Receiver for Windows
- Download Citrix Receiver for Windows (CitrixReceiver.exe) from Citrix Downloads.
- Log onto the client device with administrator privilege.
- You can install Citrix Receiver for Windows in two ways:
Using the Graphical User Interface Using the Command Line Interface - Double-click CitrixReceiver.exe.
- In the Citrix Receiver Installation wizard, select Enable Single Sign-on.
- Click Next.
- After the installation is complete, log off from the client device and log on again.
- Open a command prompt as an administrator and change to the directory to where CitrixReceiver.exe is located.
- Run the following command to install Citrix Receiver for Windows with the Single Sign-on feature enabled:
CitrixReceiver.exe /includeSSON /silent
- After the installation is complete, log off from the client machine and log on again.
- Launch the Task Manager to verify that the ssonsvr.exe process is running.
Users should now be able to log on to an existing Store (or configure a new Store) using Citrix Receiver for Windows without providing credentials.
Group policy settings
Configuration described in this section is required in two cases:
- When access to StoreWeb using Internet Explorer (IE) is required.
- Citrix Receiver for Windows version 4.3 or earlier.
For newer versions of Receiver (4.4 onwards) that do not require IE access, the configuration is optional
On Citrix Receiver for Windows 4.3 and Earlier:
An additional configuration is required in the Group policy settings as described below:Using Citrix Receiver for Windows Group Policy template files
Add Citrix Receiver for Windows template files to the Local Group Policy Editor. For more information, see Configure Receiver with the Group Policy Object template. Be sure to use the ADM template of the same version as the Receiver on the Client.
- Open Local Group Policy Editor by running the gpedit.msc command. Navigate to Citrix Receiver > User authentication.
- Open the Local user name password policy.
- Select Enable pass-through authentication and Allow pass-through authentication for all ICA connections.
- Click Apply and OK.
Note: If the existing version of Citrix Receiver for Windows does not have the Single Sign-on component installed, upgrading to the latest version with the /includeSSON switch is not supported.
After the installation is complete, log off from the client device and log on again.
Citrix Receiver Internet Explorer 11
Single Sign-on Diagnostics
In Citrix Receiver for Windows Version 4.5, you can use Configuration Checker to diagnose the Single Sign-on configuration.
Right-click the Citrix Receiver icon in the notification area and select Advanced Preferences > Configuration Checker.
The Configuration Checker window appears.Select SSONChecker and click Run.
The test runs on all the SSON checkpoints.
After the test is complete, the results are displayed for each test.
The test describes if all the configuration requirements for Single Sign-on are met.
For more information, see Using Configuration Checker to validate Single Sign-on configuration
Verify the list of Network Providers
If users face any issues with Single Sign-on, Citrix recommends that you verify the list of network providers list on the client machin e as described below:
Click Start.
Enter View network connections. The Network Connection window appears.
Press ALT to display the menu. Click Advanced > Advanced Settings
Advanced Settings window appears.Click the Provider Order tab.
Move “Citrix Single Sign On” to the top of the list to change the order of network providers.
